Sending Mixed Signals
Description
Author: @Jstith
Turns out the Houthi PC Small Group was only the tip of the iceberg…
REMINDER: Brute force guessing is NOT permitted.
Press the Start button begin this challenge.
OSINT Time
Here is what we got after strating and accessing the webpage: 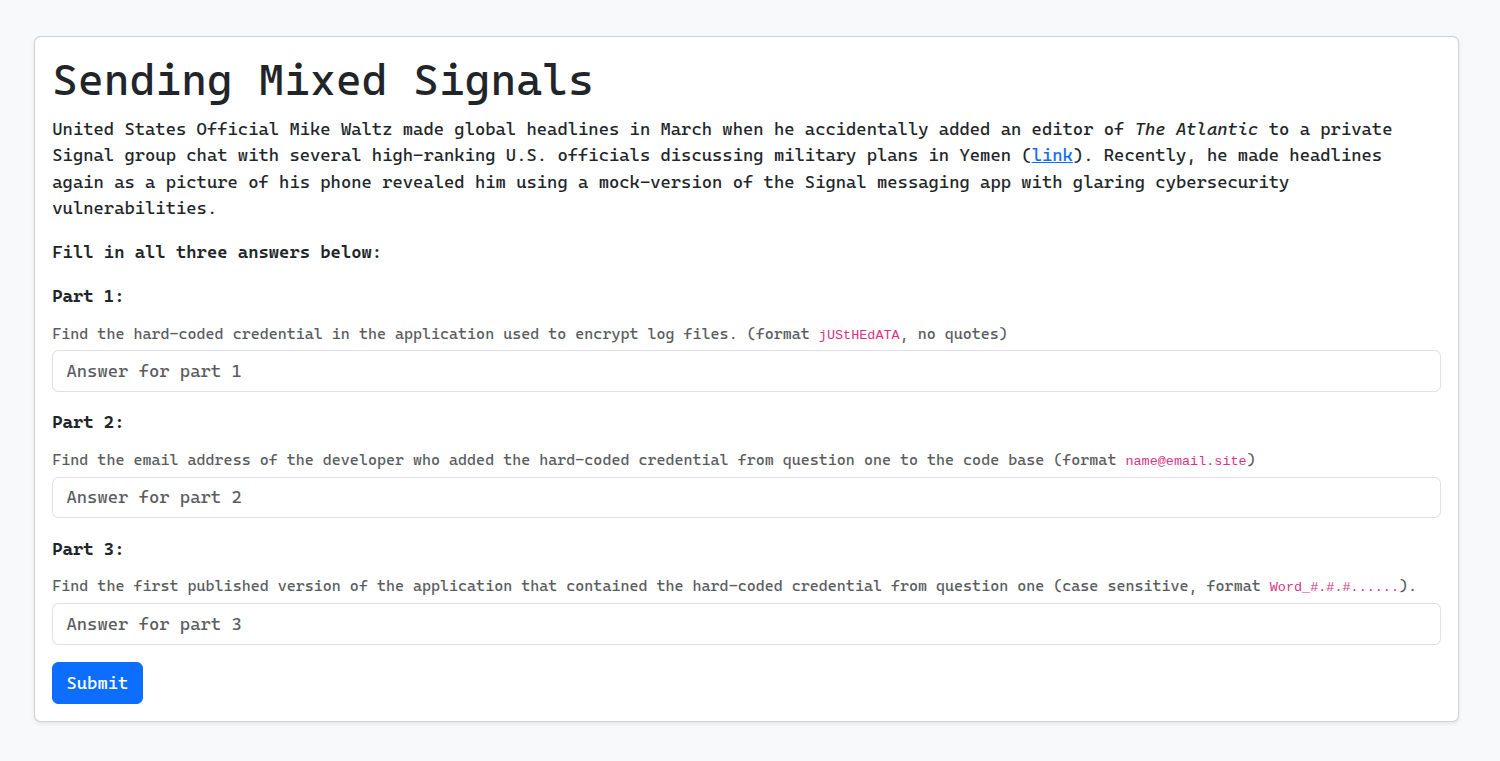
Part 1
Find the hard-coded credential in the application used to encrypt log files. (format
jUStHEdATA, no quotes)
So we did some research online looking for Find the hard-coded credential in the application used to encrypt log files signal app scandal We found this link1 for the first answer which was the following key as shown in the picture, we found the repository and went there for more enumeration2 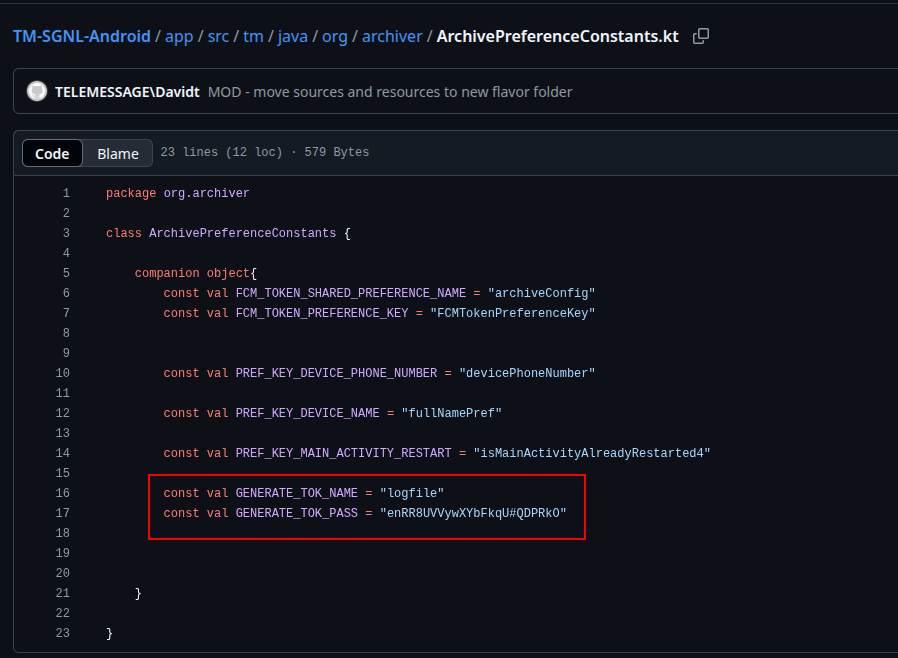 Here is the hard-coded credential in the application used to encrypt log files:
Here is the hard-coded credential in the application used to encrypt log files:
1
enRR8UVVywXYbFkqU#QDPRkO
Part 2
Find the email address of the developer who added the hard-coded credential from question one to the code base (format
name@email.site)
Now we can go further and look for the email account of the developer wjp added the hard-coded credentials from question one to the code base. For that we kept reading the article and found the following line: 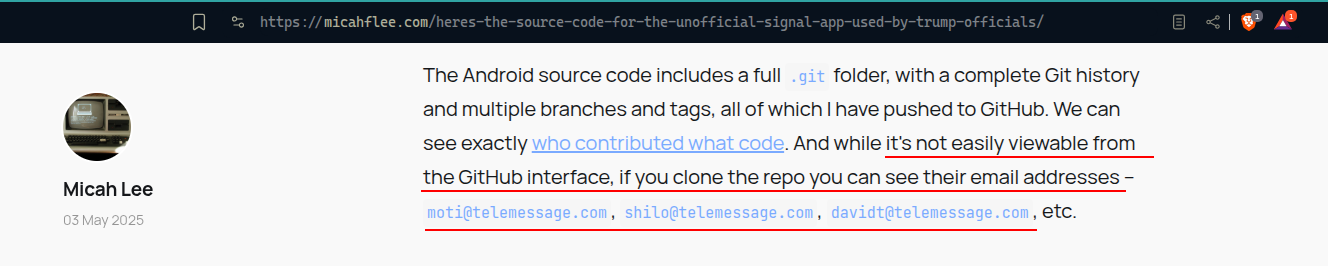 Then we had to clone the repo in order to see who did what:
Then we had to clone the repo in order to see who did what:
1
git clone https://github.com/micahflee/TM-SGNL-Android
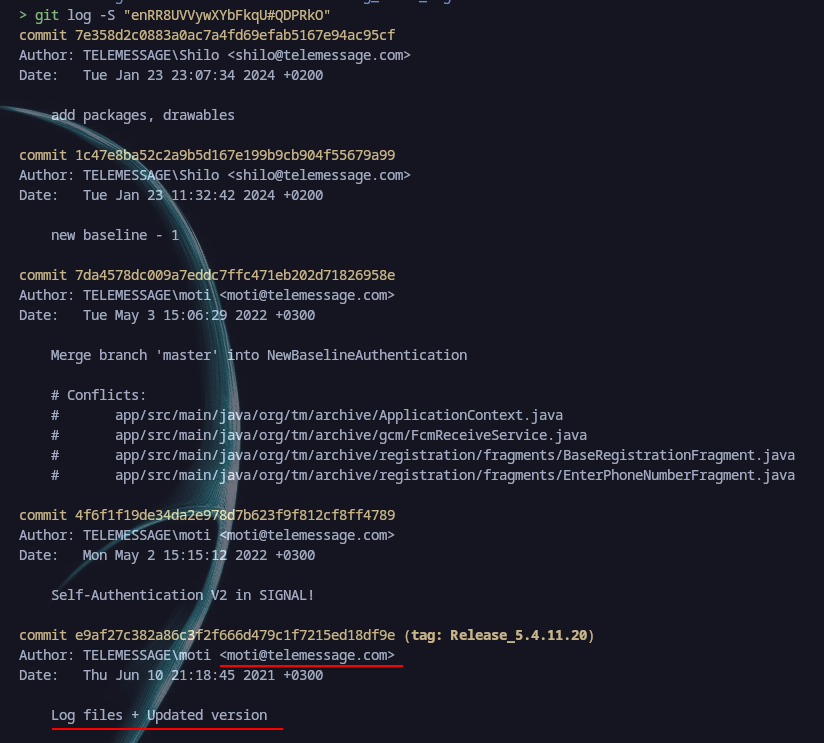
So we needed the commit hash in order to disclose that info, we got it the website here3 as shown below: 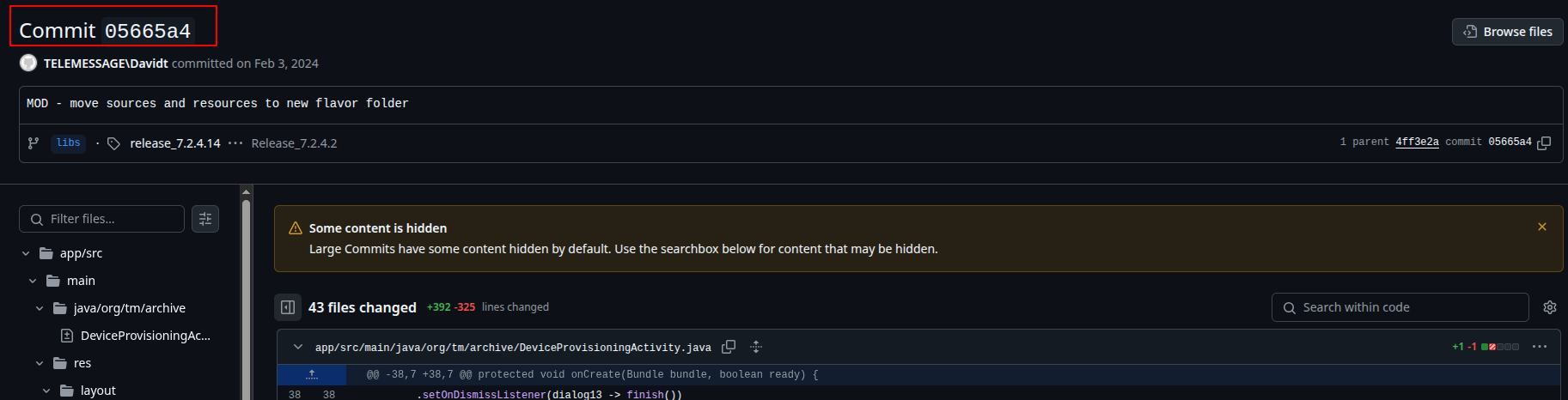 Then we can run the following command, since we have a huge repository we need to specify the string in which we want to search for:
Then we can run the following command, since we have a huge repository we need to specify the string in which we want to search for:
1
git log -S "enRR8UVVywXYbFkqU#QDPRkO"
We found the correct email:
1
moti@telemessage.com
Part 3
Find the first published version of the application that contained the hard-coded credential from question one (case sensitive, format Word_#.#.#……).
We ran:
1
git log -S "enRR8UVVywXYbFkqU#QDPRkO" --oneline
And got: 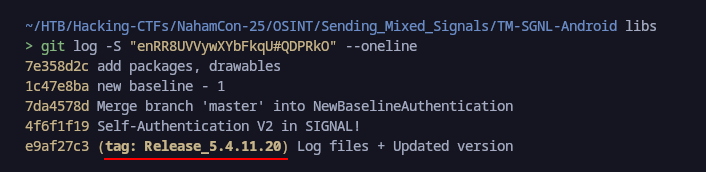 Adding this we got the last answer correct:
Adding this we got the last answer correct:  Got the flag and solved the challenge.
Got the flag and solved the challenge.
Flag
flag{96143e18131e48f4c937719992b742d7}